Behavior
Dashboard vs. Helm chart configuration
By default, the following options are configurable via your dashboard:
- Action on failure - Select whether to monitor or block resources that fail the policy check (defaults to "monitor").
- Active policy - The name of the policy to check (defaults to "Starter").
- Bypass permissions - Users/groups/ServiceAccounts that are able to bypass a failing policy check.
- Ignored resources - Resources to be ignored, in regex format, specified by namespace/kind/name or any combination of the three. See examples here.
If you wish to control these options via the Datree Helm chart instead, you can do so by changing the value of the configFromHelm parameter:
# values.yaml
datree:
configFromHelm: true
Then apply your updated values.yaml file:
helm upgrade -n datree -f values.yaml datree-webhook datree-webhook/datree-admission-webhook
Now you can control the parameters described in the table below via your Helm chart.
To update your dashboard and reflect the changes, run a manual scan.
- When controlling these options via the dashboard, changing them via the Helm chart will have no effect.
- All other configuration options (see table below) are always controlled via the helm chart.
Options
The following options (Helm chart parameters) are available for configuring Datree's behavior:
| Option | Description | Type |
|---|---|---|
configFromHelm | Determines whether the options listed here are managed from Helm chart or from the dashboard (default: false) | boolean |
enforce | Block resources that fail the policy check from being applied to the cluster. Relevant only if configFromHelm is true | boolean |
policy | The name of the policy to check, e.g: "Argo". Relevant only if configFromHelm is true | string |
bypassPermissions | Users/groups/ServiceAccounts that are able to bypass a failing policy check. See bypass permissions for details. Relevant only if configFromHelm is true | object |
customSkipList | Skip resources by namespace/kind/name. See custom skipping for details. Relevant only if configFromHelm is true | object |
enabledWarnings | The types of warnings (logs) to be printed. See Customize warnings for details and possible values. | string[] |
clusterName | The name of the cluster to be displayed in your dashboard | string |
scanIntervalHours | The number of hours between cluster scans | number |
existingSecret | A reference to a Secret object containing a Datree token | object |
token | The token used to link the CLI to your dashboard | string |
verbose | Display 'How to Fix' link for failed rules in output | boolean |
output | The format output of the policy check results: yaml, json, xml, simple, JUnit, sarif | string |
noRecord | Don’t send policy checks metadata to the dashboard | boolean |
affinity | Offers more expressive syntax for fine-grained control of how Pods are scheduled to specific nodes | object |
nodeSelector | Used to select on which node a pod is scheduled to run | object |
ℹ️ For the full list of configurable parameters in the Datree helm chart, click here
Configure options
To set/change one or more options, change the desired parameter(s) in your values.yaml file, then apply it:
# values.yaml
datree:
enforce: true
helm upgrade -n datree -f values.yaml datree-webhook datree-webhook/datree-admission-webhook
Set/change token
To change your token, you can simply change the datree.token parameter in your values.yaml file and apply it using the command mentioned above.
If you're looking for a more secure approach, use the datree.existingSecret parameter:
- Create a
Secretobject containing your token and apply it to your cluster. - Set the Secret's data in the
datree.existingSecretparameter in yourvalues.yamlfile:
# values.yaml
datree:
existingSecret:
name: <secret-name>
key: <secret-key>
- Apply
values.yamlto your cluster.
If both options are set, datree.existingSecret will take precedence.
Bypass permissions
You can configure Datree to allow certain users/groups/ServiceAccounts to bypass a failing policy check.
To add entities to the bypass permissions list, add/change the datree.bypassPermissions parameter in your values.yaml file. For example:
datree:
bypassPermissions:
userAccounts:
- "minikube"
serviceAccounts:
- "system:serviceaccount:default:srv"
groups:
- developers
Custom skipping
Datree can be configured to skip certain rules/resources by using a dedicated ConfigMap.
The ConfigMap is a part of the Datree Helm chart, under the parameter datree.customSkipList.
You can use it to skip a namespace, kind, name, or any combination of the three.
To add an entry to the ConfigMap:
1. In your values.yaml file, add the following parameter:
datree:
customSkipList:
- "(.*);(.*);(.*)" # "namespace;kind;name"
Replace (.*);(.*);(.*) with your desired values (see examples below). You can use a regular expression for any of the aformentioned properties.
2. Apply your values.yaml file:
helm upgrade -n datree -f values.yaml datree-webhook datree-webhook/datree-admission-webhook
By default, Datree skips all resources with a name starting with aws-node.
This entry is already included in the default values.yaml file.
Example patterns
The following pattern will cause Datree to skip all resources in the namespace 'myNs':
myNs;(.*);(.*)
The following pattern will cause Datree to skip all resources of kind ServiceAccount, regardless of their namespace:
(.*);ServiceAccount;(.*)
The following pattern will cause Datree to skip all resources in all namespaces if the resource name starts with the prefix 'appName-':
(.*);(.*);(^appName-.*)
Ignore a namespace
Add the label "admission.datree/validate=skip" to the configuration of the namespace you would like to ignore:
kubectl label namespaces default "admission.datree/validate=skip"
To delete the label and resume running the datree webhook on the namespace again:
kubectl label namespaces default "admission.datree/validate-"
Skip specific rules for a single object
To skip a rule for a specific object, add the following annotation to its manifest:
datree.skip/[identifier]: [message]
identifier - the unique rule identifier.
message - optional text to be presented in the policy check output (CLI and activity-log tab at the dashboard).
To obtain identifiers of built-in rules, go to your dashboard and click on the 'i' icon of your desired rule:
This will lead you to the documentation of the rule, where you will find the identifier:
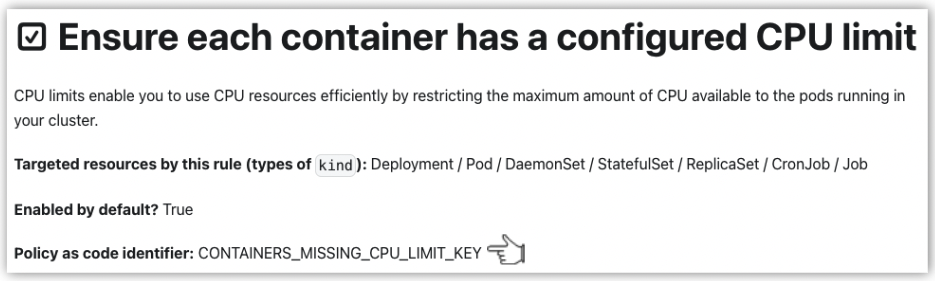
Identifiers of custom rules can be found in the policy.yaml file, when in Policy-as-code mode. For example:
customRules:
- identifier: CUSTOM_WORKLOAD_INCORRECT_ENVIRONMENT_LABELS
name: Ensure correct environment labels are used [CUSTOM RULE]
defaultMessageOnFailure: Use only approved environment labels ('prod', 'staging' and 'test')
schema:
Example of a Deployment with skipped rules:
apiVersion: apps/v1
kind: Deployment
metadata:
name: rss-site
namespace: test
labels:
environment: prod
app: web
annotations:
datree.skip/WORKLOAD_INVALID_LABELS_VALUE: irrelevant for deployments, skipping.
datree.skip/CONTAINERS_MISSING_LIVENESSPROBE_KEY: irrelevant for prod environment, skipping.
annotations have a character limit - the key and value of an annotation cannot exceed 63 characters each.
For more information, see the Kubernetes docs
Customize warnings (logs)
By default, Datree prints a warning for all types of events, as described in the table below.
The Helm chart parameter datree.enabledWarnings allows you to customize which types of warnings are printed, simply delete the ones you do not wish to see, and apply your values.yaml file.
| Warning | Description | Helm chart value |
|---|---|---|
| Passed policy checks | Resources that passed the policy check | passedPolicyCheck |
| Failed policy checks | Resources that failed the policy check | failedPolicyCheck |
| RBAC-bypassed | Resources that were bypassed | RBACBypassed |
| Skipped resources | Resources that were skipped | skippedBySkipList |
An example of a failed policy check warning:

Update
To update Datree to the latest version, run the following commands:
helm repo update
helm upgrade -n datree datree-webhook datree-webhook/datree-admission-webhook --set datree.token=<YOUR_DATREE_TOKEN> --set datree.clusterName=<DESIRED_CLUSTER_NAME> --debug
To avoid having to write your token and cluster name explicity, you can use a values.yaml file to hold them, then apply it using the -f flag when upgrading Datree.
For example:
# values.yaml
datree:
token: a1b2c3d4e5f6g7h8i9
clusterName: aws-stg1
Multiple policies
You may want to use different policies for different namespaces. To do so, follow these steps (examples below):
- Instruct Datree to be configured from the Helm chart by setting
datree.configFromHelmtotrue. - Delete the
datree.policyparameter from the chart, and instead adddatree.multiplePolicies, which is an array of objects. - Each item in the array needs to have the following parameters:
policy(mandatory) - the name of the policy (e.g. "Starter").namespaces- an object containing the following parameters:includePatterns(mandatory) - an array of regex patterns for namespaces to include.excludePatterns- an array of regex patterns for namespaces to exclude.
The following example will set the policy "Starter" for all namespaces except "security":
datree:
configFromHelm: true
# policy: "Starter" (This parameter should be deleted)
multiplePolicies:
- policy: "Starter"
namespaces:
includePatterns:
- ".*"
excludePatterns:
- "security"
The following example will set the policy "CIS" for namespaces "ns1" and "ns2", and the policy "Starter" for namespace "ns3":
datree:
configFromHelm: true
multiplePolicies:
- policy: "CIS"
namespaces:
includePattern:
- "ns1"
- "ns2"
- policy: "Starter"
namespaces:
includePattern:
- "ns3"
Each policy can be written only once in the multiplePolicies array.
To use the same policy for more than one namespace, specify the desired namespaces under the includePattern key (see "ns1" and "ns2" in the example above).
Uninstall
To uninstall Datree, run the following commands:
helm uninstall datree-webhook -n datree
kubectl delete ns datree