Getting started
The Datree CLI is a versatile tool, allowing you to scan your k8s configs during development, as a pre-commit hook, and/or as part of your CI. Use the CLI to ensure no misconfigurations make it into your codebase.
No prerequisites to get started!
1. Install the Datree CLI
Binary releases can be downloaded from the releases page or can be installed directly
- Linux
- MacOS
- Windows (PowerShell)
- Homebrew
- Docker
- Other
curl https://get.datree.io | /bin/bash
curl https://get.datree.io | /bin/bash
iwr -useb https://get.datree.io/windows_install.ps1 | iex
brew tap datreeio/datree
brew install datreeio/datree/datree
docker pull datree/datree
The following packages are not maintained by Datree, and therefore may not be up to date.
MacPorts
sudo port install datree
2. Run a policy check against a Kubernetes manifest
Run the CLI against any Kubernetes YAML file.
You can use our demo file if you wish:
- Linux
- MacOS
- Windows (PowerShell)
- Docker
datree test ~/.datree/k8s-demo.yaml
datree test ~/.datree/k8s-demo.yaml
datree.exe test $env:USERPROFILE\.datree\k8s-demo.yaml
cat ~/.datree/k8s-demo.yaml | docker run -i datree/datree test -
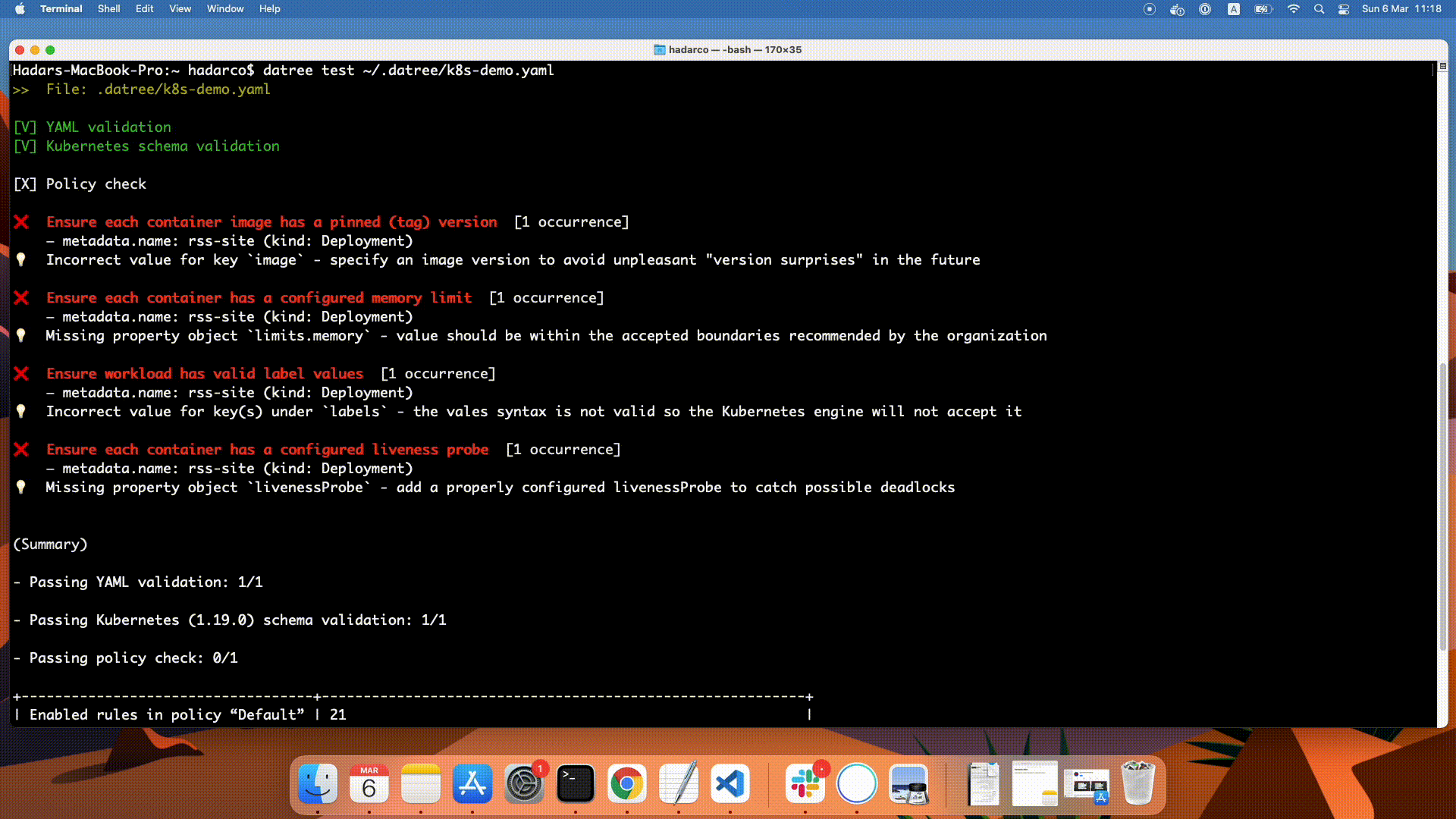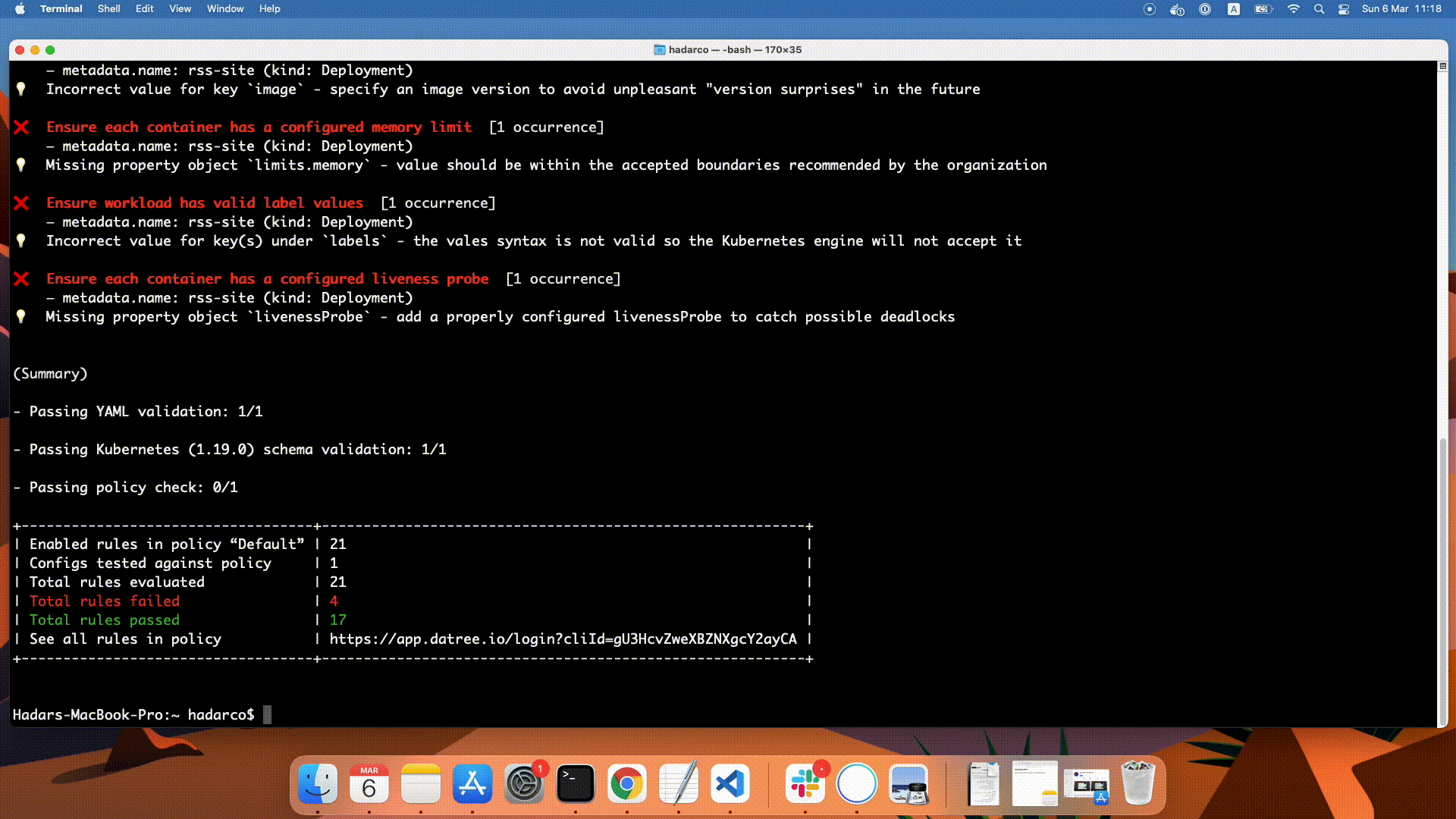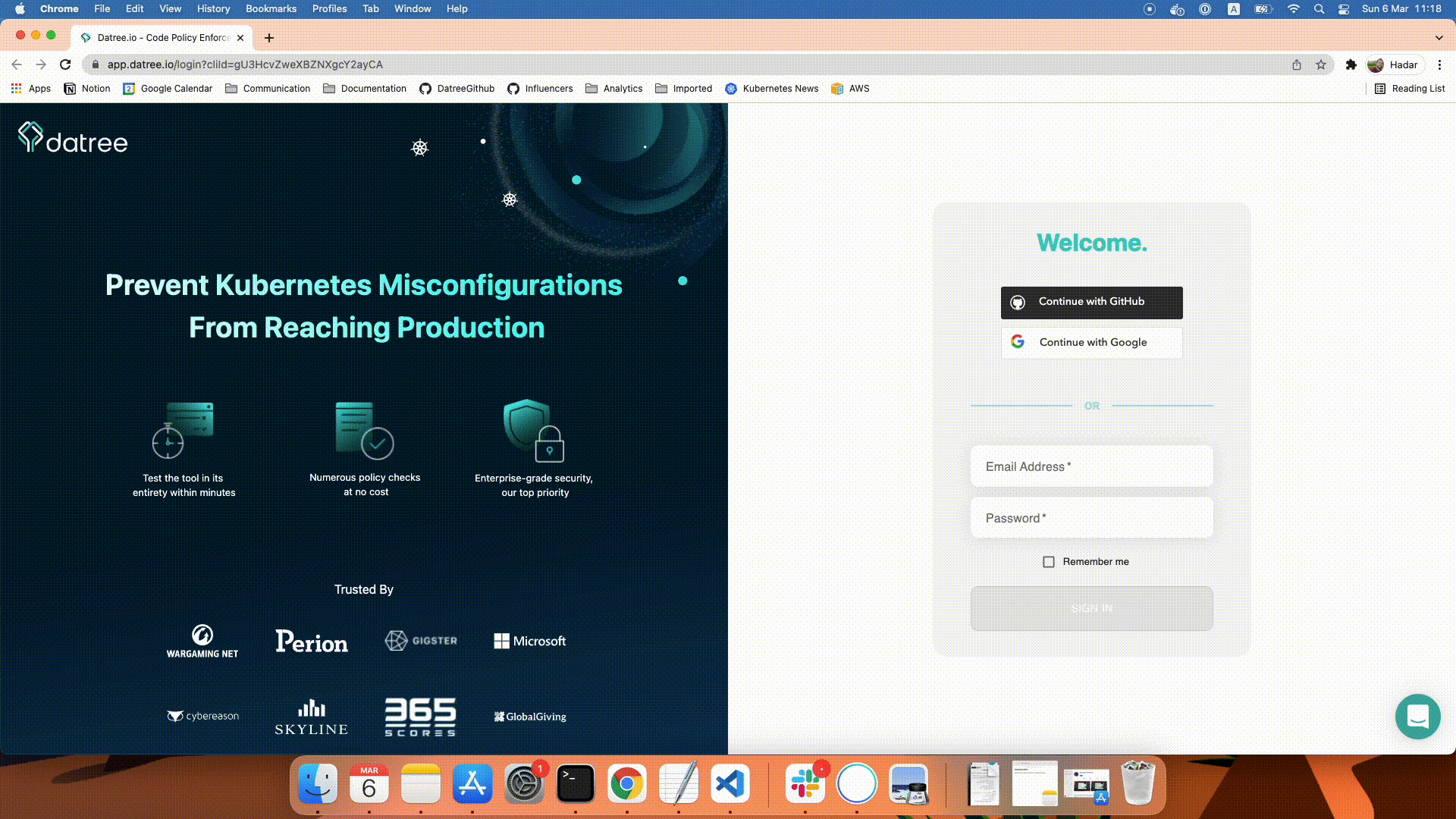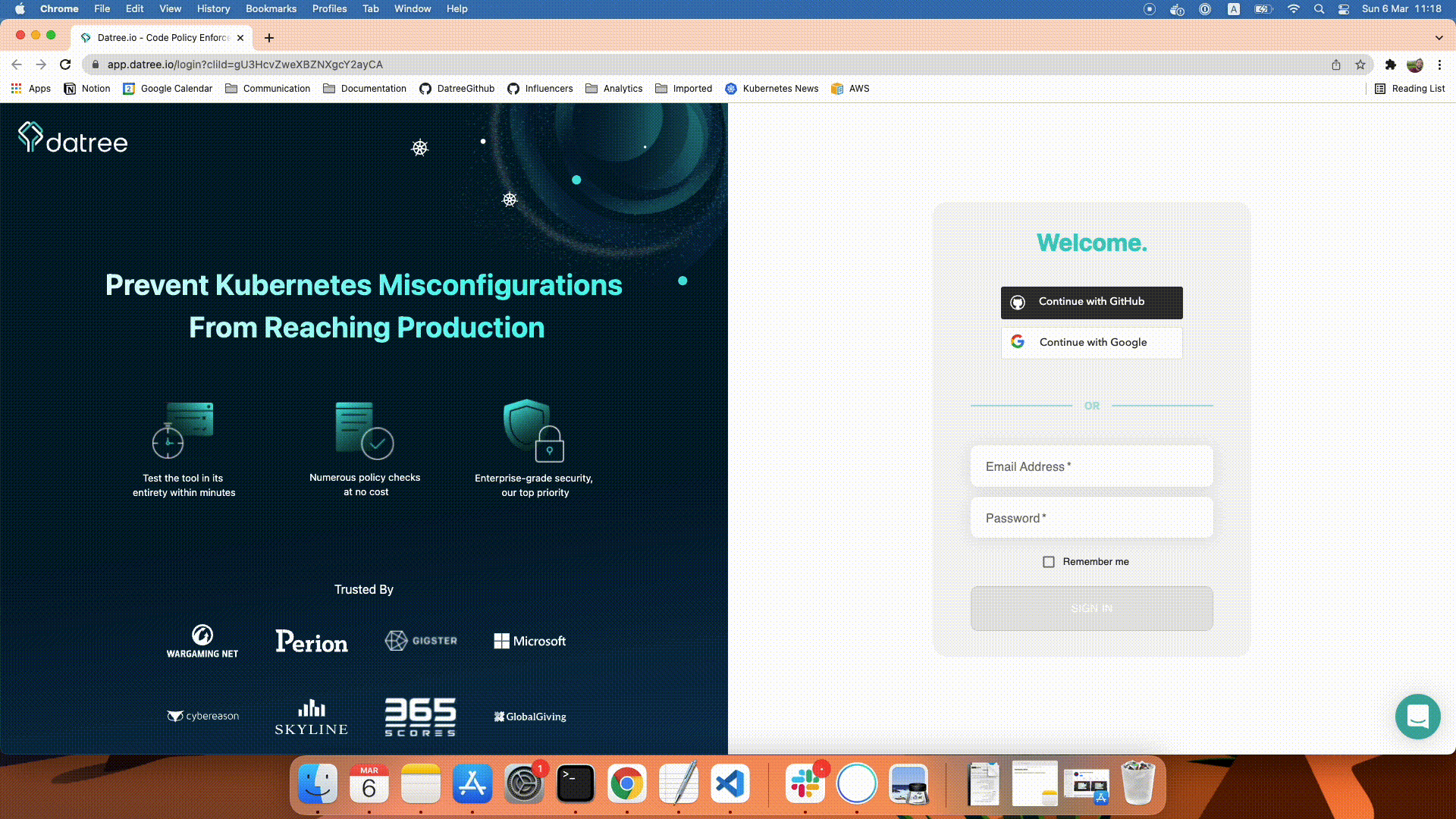
You will get the following output in your CLI:
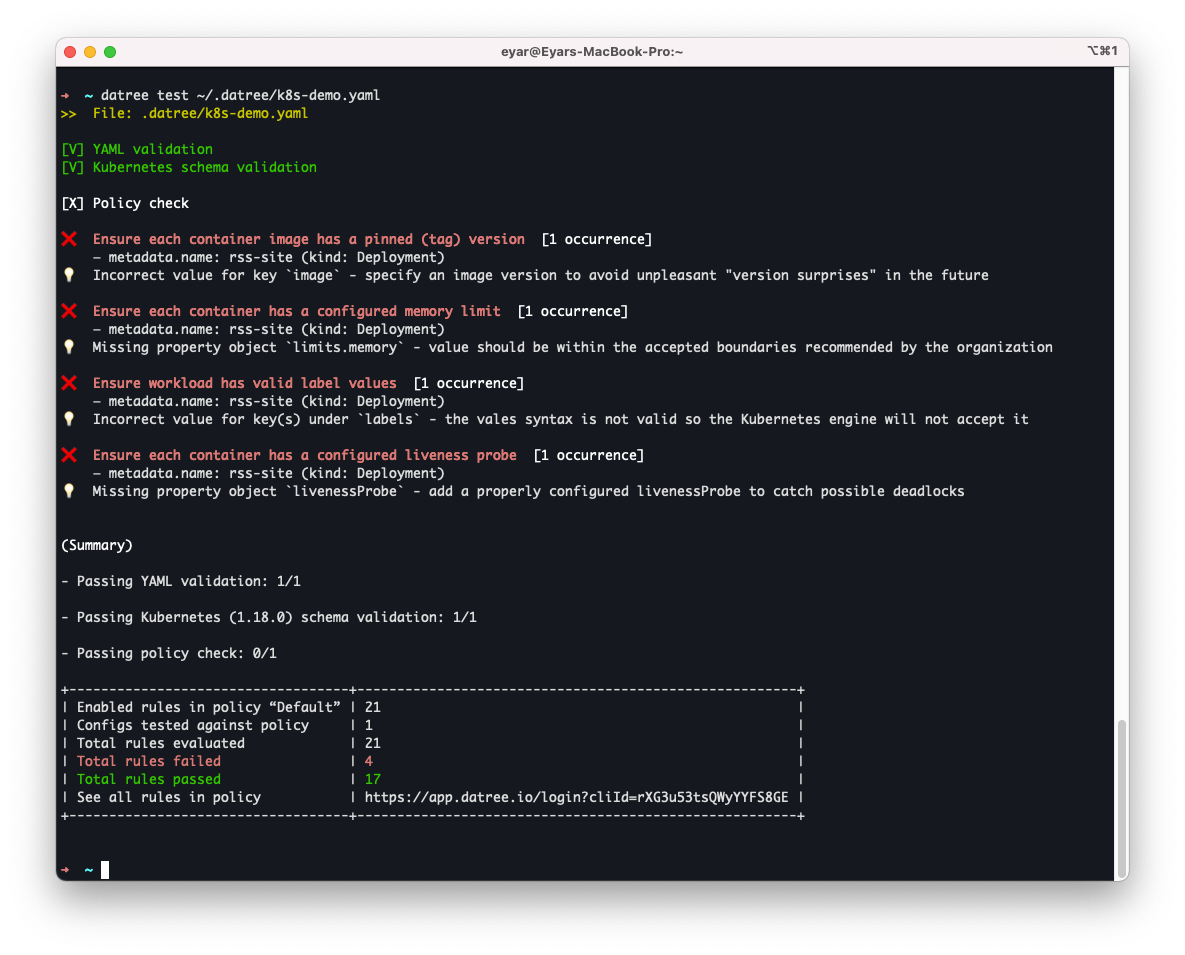
3. Customize your policy
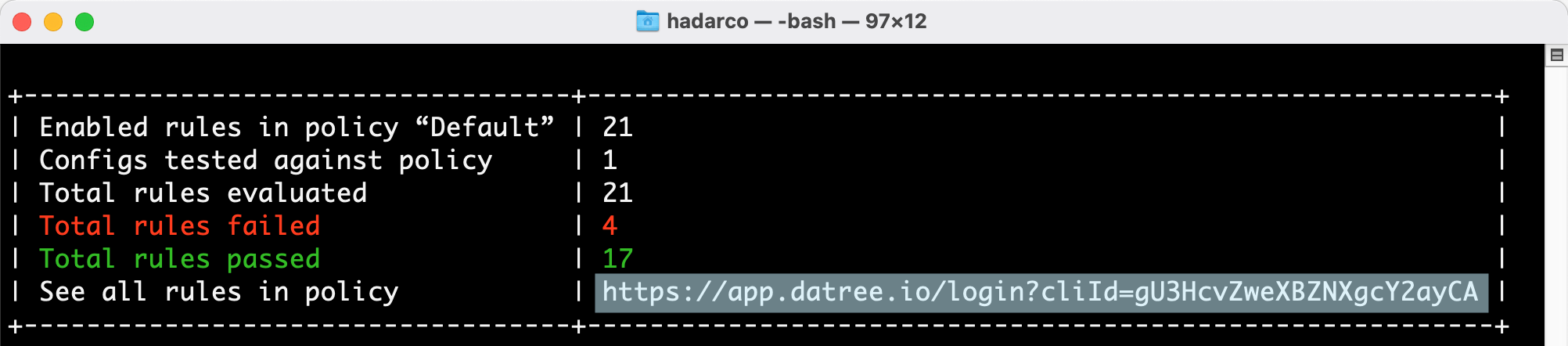
Connect your CLI to your dashboard
Follow the link in the output summary:
To start using your dashboard, easily sign-up using your private GitHub or Google account, no need to enter any personal information.
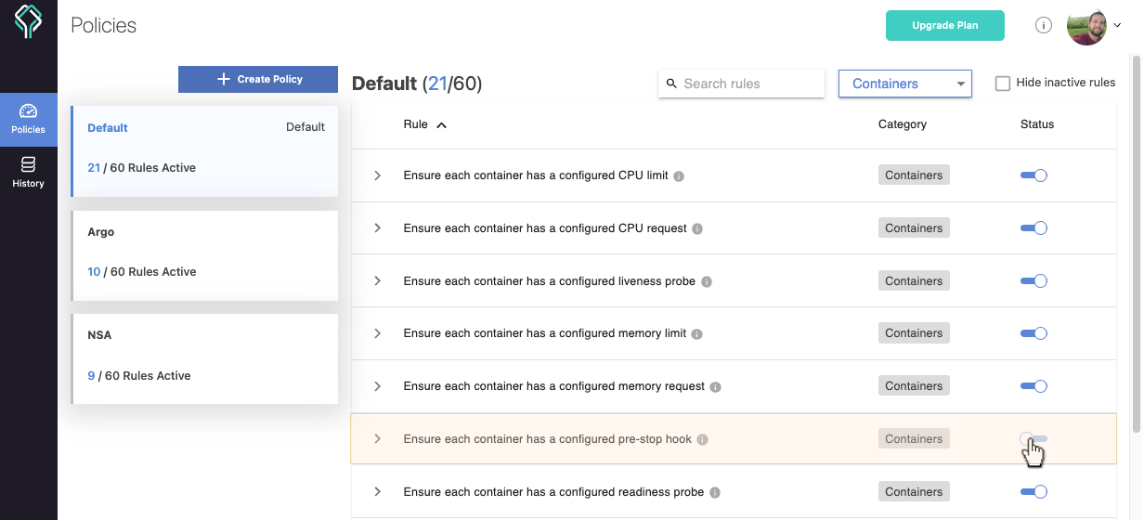
Enable/disable built-in rules
After signing up, you'll be automatically redirected to your Centralized policy where you can configure it according to your needs:
[OPTIONAL] Add your custom rules
In addition to the tool's built-in rules, you can also write any rule that you wish and run it against your Kubernetes configurations to check for violations. Read how to set up custom rules at Understanding custom rules.
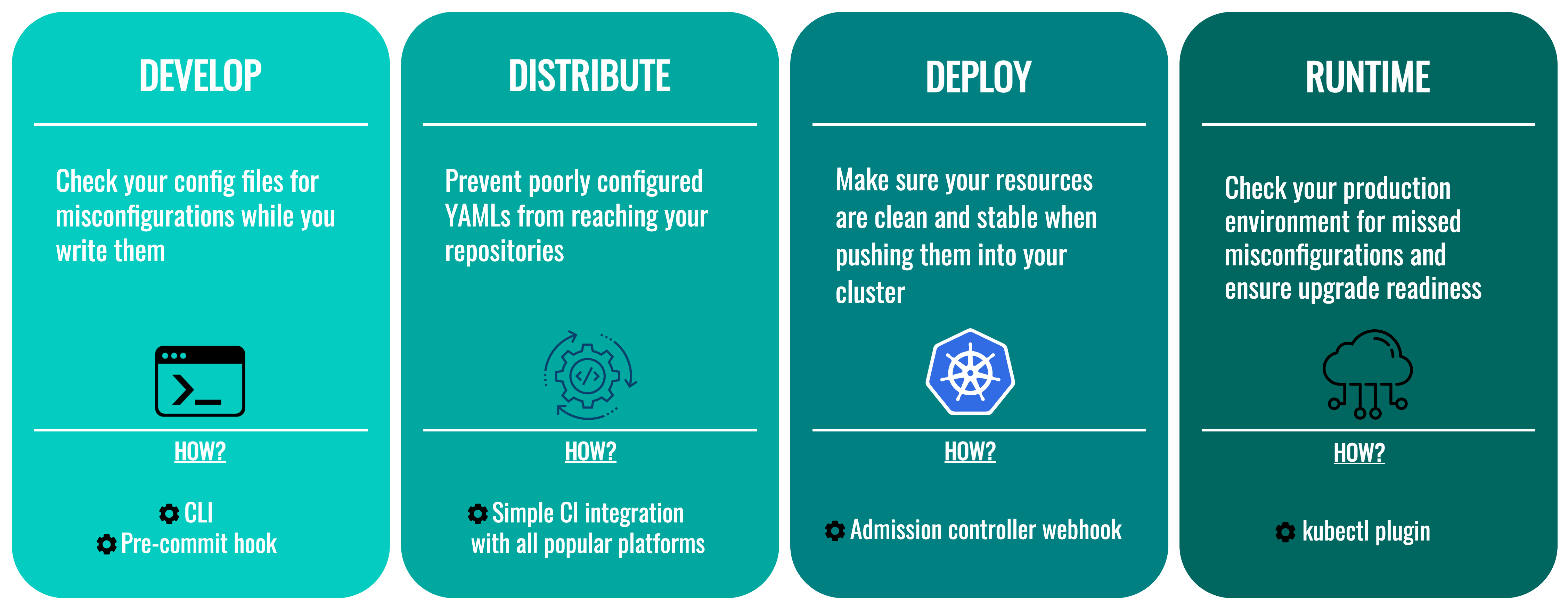
4. Integrate into your workflow
From develop to runtime, you can use Datree in every step of your Kuberenetes pipeline to help you prevent misconfigurations:
⏩ Develop (code) - run the CLI locally (or as a pre-commit hook) to get instant validation
⏩ Distribute (CI) - integrate with your CI platform to shift-left policy checks
⏩ Deploy (CD) - gate your cluster with the admission webhook
⏩ Runtime (production) - query deployed resources with the kubectl plugin to your know your status